How do you money an IP on a server? (or how to stop spam)

Lately I have started to pay more attention to what is happening on the blogs on the server. I noticed that I have a very read blog, with a lot of hits. An obvious example is in the image below:
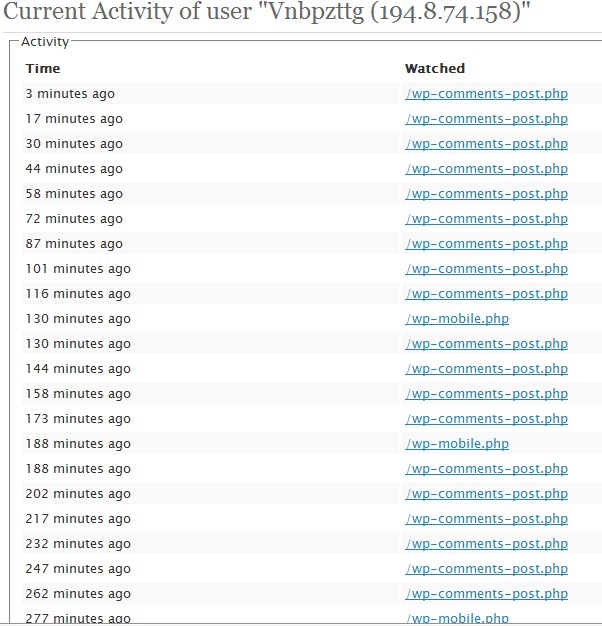
Such spam bots there are many of them, and their comments add up by the hundreds Acism. I know that in WordPress, there is its option block an IP who wants to comment, but this does not help much, for two reasons.
1. The IP if it is blocked from WordPress –> Dashboard, reaches the server and there is traffic.
2. If there are 100 blogs on a server... each one must block the same IP. (headaches)
3. From the same IP, he can try to look for vulnerable security points, on other open ports. (I know I said two reasons. One is a bonus)
Another method to block the access of an IP to a site is to edit the file .htaccess, from the root folder, where the website files are found (usually public_html). I had fantasies like this, around June 2007, when I was writing the post "Deny Access to Spammer IP”.
I don't recommend the .htaccess IP blocking method to anyone, for one reason: the more loaded the .htaccess file is, the longer the site's loading time increases. If 100 .htaccess files would have 50 directives each, on Apache (HTTP Server), you can put candies and two candles :)
I think the third method is the best. IP blocking-s at the level of server, all of them ports, using iptables.
In the image above, the IP 194.8.74.158 is seen, trying to spam some blog pages. Blocking it, at the server level, is done in the following way.
root@server [~]# /sbin/iptables -I INPUT -s 194.8.74.158 -j DROP
root@server [~]# /sbin/service iptables save
Saving firewall rules to /etc/sysconfig/iptables: [ OK ]
root@server [~]#Of course, we will not block each individual IP. From what I have seen, the bots use several IPs from the same block. In this case there is ARIN and RIPE.
whois (ripe.net) : 194.8.74.158
inetnum: 194.8.74.0 - 194.8.75.255
netname: DRAGONARA-NET
descr: Dragonara Alliance Ltd
country: GBOK. If the IP comes from a region where I'm sure I don't want visitors on the server (either via the web or via email), I have the option to block the access of two classes C (Class C subnet), which includes the entire range of IPs between 194.8.74.0 and 194.8.75.255.
/sbin/iptables -I INPUT -s 194.8.74.0/24 -j DROP
/sbin/iptables -I INPUT -s 194.8.75.0/24 -j DROP
/sbin/service iptables saveiptables –L , to see the list of "Chain INPUT" IPs.
How do you money an IP on a server? (or how to stop spam)
What’s New
About Stealth
Passionate about technology, I write with pleasure on stealthsetts.com starting with 2006. I have a rich experience in operating systems: Macos, Windows and Linux, but also in programming languages and blogging platforms (WordPress) and for online stores (WooCommerce, Magento, Presashop).
View all posts by StealthYou may also be interested in...

